


This nightmare scenario isn’t fiction—it’s happening to Indonesian businesses every single day. While you’re reading this sentence, cybercriminals are already inside networks across Jakarta, Surabaya, Gresik, Sidoarjo, and Mojokerto, quietly stealing data, mapping systems, and preparing devastating attacks.
But here’s the plot twist that separates the victims from the survivors: The companies that survive already know exactly where their vulnerabilities are—because they hired professional hackers to find them first.
This is your complete survival guide to join the protected elite.
Let me share some numbers that will make your blood run cold:
The Daily Digital Assault on Indonesia:
1.85 BILLION cyberattack attempts in 2023 alone
11 million attacks in just Q1 2023
89 distinct hacker groups specifically hunting Indonesian businesses
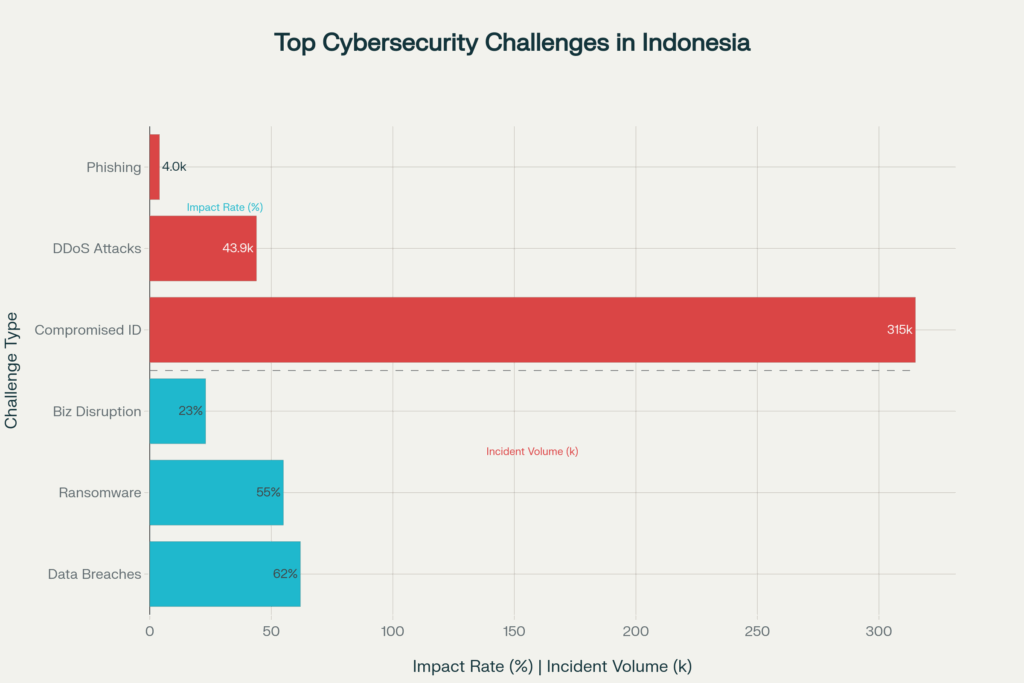
315,000 stolen passwords in 6 months
$8 million ransom demand for Indonesia’s National Data Center
Only 11% of Indonesian companies have proper cybersecurity
But here’s the statistic that should terrify every business owner: 60% of small businesses that suffer a cyberattack permanently close their doors within 6 months.
Jakarta: The Digital Fort Knox
Jakarta isn’t just Indonesia’s capital—it’s the cybercriminal equivalent of hitting the jackpot. Every single day, this digital goldmine processes:
Trillions of rupiah in financial transactions
Personal data of 10+ million citizens
Critical government and military communications
The beating heart of Southeast Asia’s digital economy
When hackers hit Jakarta, they don’t just steal data—they can cripple the entire Indonesian economy.
Surabaya & East Java: The Industrial Jackpot
The East Java industrial corridor represents something even more valuable to cybercriminals: the power to bring Indonesia’s manufacturing sector to its knees. One successful attack can:
Shut down supply chains worth billions
Halt port operations affecting international trade
Disrupt chemical and energy facilities
Cripple government services for millions of citizens
The June 2024 Reality Check: When hackers attacked Surabaya’s National Data Center, they didn’t just hit one building—they paralyzed services for over 200 government agencies simultaneously. Imagine if that had targeted the industrial supply chains connecting Gresik, Sidoarjo, and Mojokerto.
The Ostrich CEO: “Cyber-What Now?”
Believes “We’re too small to be targeted” (while 68% of attacks hit small businesses)
Thinks antivirus software = complete protection
Views cybersecurity as “just an IT problem”
Wake-up call coming: Usually at 3 AM with a ransom demand
The Worried Executive: “I Know We’re Screwed, But…”
Loses sleep knowing they’re vulnerable
Overwhelmed by technical jargon and options
Paralyzed by fear of costs and business disruption
You’re not alone: This guide is specifically designed to help you
The Cyber-Warrior: “Show Me My Vulnerabilities”
Takes cybersecurity as seriously as fire insurance
Ready to invest in professional protection
Wants actionable intelligence, not just scary stories
You’re ahead of the game: Skip to the advanced implementation sections
Ready to transform from vulnerable to bulletproof? Get your free cybersecurity reality check from JCSS Indonesia’s experts.
Imagine hiring the world’s best burglars to break into your office—legally and safely—to show you exactly how real criminals would do it. That’s penetration testing in a nutshell.
But instead of stealing your TV, these ethical hackers are trying to steal your customer data, bank account access, and business secrets. The difference? They’re the good guys working for you, and they hand you a detailed manual on how to lock every door they picked.
The Technical Reality Behind the Magic:
Penetration testing isn’t random button-mashing. It’s a sophisticated, systematic approach that mirrors exactly how real cybercriminals operate:
Think like an attacker so you can stop one. This compact playbook turns offensive tactics into your defensive advantage — clear, actionable, and built to harden your environment fast.
Social sleuthing: what your employees reveal on social media (and how attackers use it).
Data scavenging: uncovering leaked credentials, sensitive files, and public crumbs.
Forgotten assets: rediscover overlooked subdomains, legacy apps, and shadow systems.
Tech blueprinting: map your stack and dependencies so nothing hides in the dark.
Port & service scans: discover exposed entry points before someone else does.
Version & vuln checks: identify outdated software that invites compromise.
Web app testing: simulate real attack paths against forms, APIs, and auth.
Wireless & IoT probes: assess the messy perimeter most teams forget.
Controlled exploitation: validate findings by exploiting them in a contained way.
Privilege escalation: follow the attacker’s path from low to high access.
Lateral movement: simulate how an intruder would traverse the network.
Sensitive-data access: prove whether critical repositories are truly protected.
What was breached: clear, itemized evidence of every compromise.
Business impact: translate technical findings into real-world risk.
Step-by-step remediation: prioritized fixes anyone can follow.
Defense roadmap: strategic, long-term actions to make your environment bulletproof.
Most Indonesian businesses rely on what I call “Security Theater“—measures that look good but provide minimal real protection:
❌ The False Security Blanket:
Basic Antivirus: Catches 40% of modern threats (criminals laugh at this)
Simple Firewalls: Easily bypassed by sophisticated attackers
Password Policies: Useless when hackers steal the entire password database
Employee Training: Helpful, but one mistake opens the floodgates
Compliance Checkboxes: Meeting requirements ≠ actual security
✅ What Penetration Testing Actually Tests:
Human Psychology: Will your employees fall for sophisticated phishing?
Technical Loopholes: Can hackers bypass your firewall using legitimate protocols?
Configuration Errors: Are your “secure” systems actually misconfigured?
Physical Security: Can someone walk into your office and plug in a device?
Supply Chain Weaknesses: Can attackers use your vendors against you?
Real Indonesian Business Example:
A Jakarta e-commerce company spent millions on cybersecurity tools but left their admin panel accessible with default passwords. Penetration testing found this in 15 minutes. A criminal could have stolen 100,000 customer records. The fix cost ₹50,000—the breach would have cost ₹2 billion.
Cloud Pen Testing With cloud technology adoption accelerating cloud environments require rigorous testing. Cloud penetration testing dissects Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) for exploitable vulnerabilities like insecure APIs and weak credentials.
Network Pen Testing Network pentesting scrutinizes network infrastructures, whether on-premises or within cloud services like Azure and AWS. It covers internal, external, and wireless network assessments to detect lapses in configurations and encryption protocols.
Web Application Pen Testing As web applications proliferate, so do potential vulnerabilities. This testing simulates attacks under varying conditions—black-box, white-box, and gray-box—to identify issues such as DDoS, SQL injections, and cross-site scripting.
API Pen Testing Given their role in communication between applications, APIs require thorough testing to protect against broken authentication, data exposure, and other critical vulnerabilities.
Mobile Pen Testing Addressing vulnerabilities in mobile applications for Android, iOS, and hybrid systems is vital. Key issues include insecure communications and weak authentication protocols.
Social Engineering Pen Testing Unlike technological testing, social engineering focuses on human vulnerabilities, employing tactics like phishing and pretexting to evaluate organizational resilience and guide training improvements.
Penetration testing is carried out by cybersecurity experts skilled in identifying and exploiting security flaws. These experts may be in-house staff or external specialists from VAPT companies, depending on the organization’s preference for expertise and objectivity.
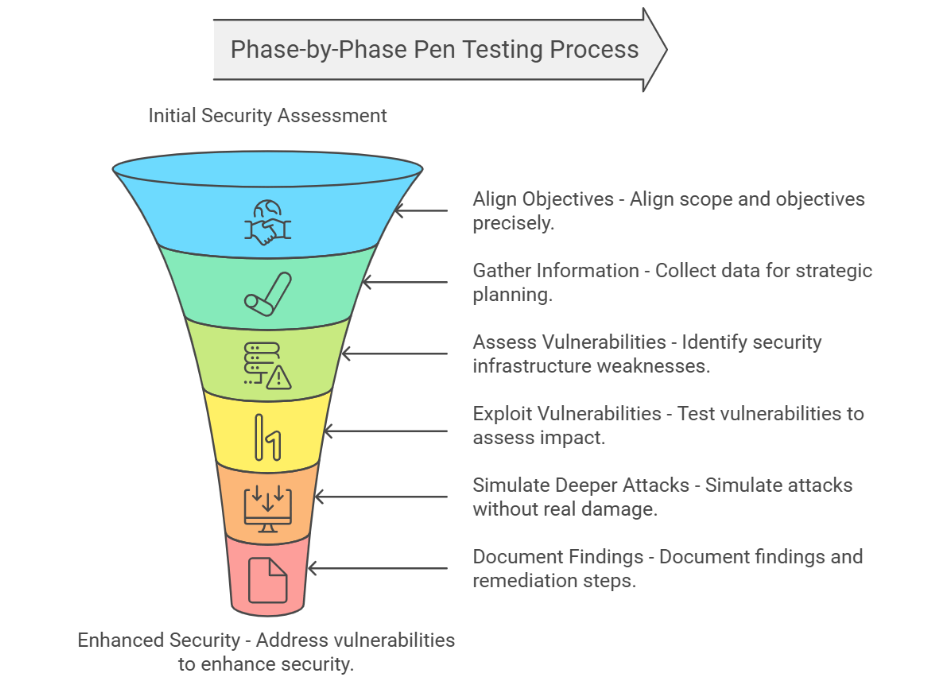
Pre-Engagement Analysis Align your security provider on scope and objectives before executing tests.
Information Gathering Collect publicly available data to assist in crafting effective penetration strategies.
Vulnerability Assessment Identify potential security lapses within the organization’s infrastructure.
Exploitation Exploit identified vulnerabilities to assess their impact and potential exploitation ease.
Post-exploitation Simulate deeper attacks to measure impact without causing real damage.
Reporting Document findings alongside remedial steps for management and technical teams.
Resolution Act on reported vulnerabilities to safeguard systems against breaches.
Rescanning Validate the resolution of vulnerabilities through rescanning efforts to affirm security improvements.
White Box Testing Full disclosure to testers ensures the identification of deep and complex vulnerabilities across systems.
Gray Box Testing Partial knowledge allows testers to focus keenly on specific attack vectors while avoiding unnecessary trial-and-error methods.
Black Box Testing Mimicking real-world threat actors, black box testing is often left to third parties to effectively emulate external attacks.
Vulnerability Identification Proactively identifying exploitable vulnerabilities to prioritize security rectifications.
Enhanced Security Posture Increases the effectiveness of organizational security measures and protocols.
Compliance Achievement Aligns with industry regulations such as PCI DSS, ensuring rigorous security standard adherence.
Cost Efficiency Prevents costly breaches by addressing issues before exploitation.
Trust Building Certifications and compliance derived from regular penetration testing enhance trust among customers and partners.
Data Protection Through regular testing, organizations can safeguard sensitive data, protecting both employee and customer information from breaches.
Reputation Improvement A dedication to robust security practices, including regular penetration testing, can boost an organization’s reputation and help attract new customers and partners.
Financial Loss Prevention Considering the high cost of data breaches, estimated at $4.45 million in 2023, pen testing serves as a crucial preventative measure against financial and reputational damage.
Quick Answer: Professional ethical hackers attack your systems using real criminal techniques to find vulnerabilities before the bad guys do.
The Hollywood Explanation:
Remember the movie where the good guy hacker races against time to break into the villain’s computer? Penetration testing is exactly like that, except:
The “good guy hacker” works for YOU
They’re breaking into YOUR systems (with permission)
Instead of saving the world, they’re saving your business
They give you a detailed report instead of dramatic music
The Technical Deep-Dive (Made Simple):
Phase 1: The Stalker Phase (Reconnaissance)
Your ethical hackers become digital detectives, gathering information about your business:
What they’re looking for: Employee names, email addresses, technology used, business relationships
Where they look: Social media, company websites, job postings, public records
Why it matters: Real hackers use this info to craft convincing fake emails and calls
Example: Finding your IT manager’s LinkedIn profile to impersonate them
Phase 2: The Mapping Phase (Scanning & Enumeration)
Like burglars casing a house, hackers map your digital “building”:
Network Discovery: Finding all computers and devices on your network
Port Scanning: Testing which “doors and windows” are open
Service Identification: Understanding what software is running where
Vulnerability Detection: Identifying which systems have security flaws
Phase 3: The Break-In Phase (Exploitation)
This is where the magic happens—ethical hackers attempt controlled break-ins:
Exploit Testing: Actually trying to hack your systems (safely)
Privilege Escalation: Seeing how far they can get once inside
Lateral Movement: Testing if they can spread through your network
Data Access: Determining what sensitive information they could steal
Phase 4: The Evidence Phase (Reporting)
Unlike real criminals, ethical hackers document everything:
Proof of Compromise: Screenshots showing exactly what they accessed
Business Impact Analysis: Explaining what this means for your company
Remediation Roadmap: Step-by-step instructions to fix every problem
Executive Summary: Leadership briefing on risks and investments needed
The Amazing Result: You get a complete “heist movie script” showing exactly how criminals would rob you, plus the alarm codes to stop them.
Ready to see your business through a hacker’s eyes? Schedule your reconnaissance briefing with JCSS Indonesia.
Quick Answer: It depends on your risk level, but annually is the absolute minimum for any serious business.
The Champions League Schedule (High-Stakes Businesses):
Financial Services – Quarterly Testing (Every 3 Months)
Why: You handle money—criminals’ favorite target
Regulatory Reality: OJK requires annual testing, smart banks test quarterly
Threat Level: Sophisticated criminal organizations specifically target banks
Technical Challenge: Rapid app updates create new vulnerabilities constantly
Cost of Getting It Wrong: Average banking breach costs ₹120+ billion
Healthcare – Semi-Annual Testing (Every 6 Months)
Why: Patient data sells for ₹3.7 million per record on the dark web
Life-or-Death Reality: Ransomware can shut down life-support systems
Regulatory Pressure: Personal Data Protection Law has severe penalties
Technical Complexity: Medical devices + IT systems = vulnerability multiplication
Reputation Impact: One breach destroys decades of patient trust
E-commerce – Annual + Change-Based Testing
Why: You store customer payment data and personal information
Seasonal Reality: Test before major shopping seasons (Ramadan, Christmas)
Technical Driver: Every website update potentially introduces vulnerabilities
Compliance Requirement: PCI DSS mandates regular testing for payment processing
Customer Trust: One data breach can destroy your brand permanently
Manufacturing – Annual with OT Focus
Why: Industrial systems are increasingly connected and vulnerable
Production Reality: Cyber attacks can halt production costing ₹750,000+ per hour
Safety Concerns: Hacked industrial controls can physically harm workers
Supply Chain Impact: Your compromise affects dozens of business partners
Legacy Challenge: Old industrial systems have serious security gaps
Emergency Testing Required When:
Major System Upgrades: New systems often introduce new vulnerabilities
Mergers & Acquisitions: You inherit unknown security posture from acquired companies
Security Incidents: After any breach, you need to verify complete cleanup
Regulatory Changes: New compliance requirements need validation
Staff Changes: Departing employees may have left backdoors
The Risk-Reward Reality Check:
Quarterly Testing Investment: ₹200-600 million annually
Single Major Breach Cost: ₹5-20 billion in damages and penalties
ROI Calculation: Every ₹1 spent on testing saves ₹10+ in breach costs
Insurance Benefits: Many insurers offer 25% discounts for regular testing
Business Continuity: Continuous operations vs. catastrophic shutdown
Need a customized testing schedule for your business risk profile? Get your personalized assessment calendar from JCSS Indonesia.
Quick Answer: Focus on network, web application, and social engineering testing, with industry-specific additions based on your business type.
Your Essential Security Testing Arsenal:
Network Penetration Testing: Your Digital Perimeter Defense
What It Actually Tests:
External Attacks: How criminals would break in from the internet
Internal Threats: What damage insiders could cause
Network Segmentation: Whether different departments are properly isolated
Remote Access: How secure your VPN and remote work setup really is
The Technical Reality:
Network Testing Playbook — A clear, punchy walkthrough
Think of this as your mission map for testing the resilience of a network — from initial reconnaissance to stealth checks. Each phase has a single goal and a handful of focused checks.
Discovery Phase — “See the battlefield”
Goal: Build the most accurate picture of what’s reachable and running.
Port scanning — find the open “doors” on the network
Service enumeration — identify which services are listening behind those doors
OS fingerprinting — determine the types of systems you’ve found
Network mapping — visualize how devices connect and relate
Vulnerability Assessment — “Spot the weak points”
Goal: Surface known and suspicious issues so you can prioritize fixes.
Automated scanning — sweep for documented flaws and exposures
Manual validation — verify scanner results and remove false positives
Custom exploit research — evaluate practical risk for critical issues
Zero-day investigation — flag and document unknown/novel risks
Exploitation Phase — “Test the real impact”
Goal: Confirm how an attacker could move, escalate, or access sensitive assets (in a controlled, ethical way).
Remote code execution attempts — test whether flaws can be triggered remotely
Privilege escalation checks — verify if low-level footholds can gain higher access
Lateral movement simulation — assess how an attacker might travel across the network
Data exfiltration validation — confirm whether sensitive data could be extracted
Defense Evasion Testing — “Measure detection gaps”
Goal: Evaluate how robust detection and logging are under evasive techniques.
Firewall bypass techniques — check if access controls hold up
IDS/IPS evasion methods — test monitoring and alerting effectiveness
Antivirus circumvention checks — observe endpoint defenses under stress
Logging & monitoring avoidance — ensure events are captured and traced.
Indonesian Business Reality: With 89% of Indonesian businesses now having internet-facing systems, your external attack surface is massive. Every misconfigured router, forgotten test server, or unsecured IoT device becomes a potential entry point.
Web & Mobile Application Testing: Your Customer-Facing Fort Knox
What Gets Attacked:
Customer Portals: Login systems, account management, payment processing
Business Applications: CRM systems, inventory management, financial platforms
Mobile Apps: Banking apps, e-commerce platforms, corporate applications
APIs: The invisible data highways connecting your systems
The OWASP Top 10 Reality Check:
Network Testing Process — a clean, punchy roadmap
A crisp, step-by-step journey to test and harden networks — from discovery to stealth checks. Perfect for a slide, LinkedIn carousel, or quick briefing.
1) Discovery Phase — find the surface
Quick wins that reveal what’s exposed and how things connect.
Port scanning — spot the open “doors”.
Service enumeration — see what’s actually running behind those doors.
OS fingerprinting — figure out which systems you’re looking at.
Network mapping — draw the topology and trust paths.
2) Vulnerability Assessment — what’s weak?
Combine automated speed with human judgement to separate noise from real risk.
Automated scans for known flaws.
Manual validation to confirm and prioritize findings.
Custom exploit research to test edge cases safely.
Zero-day discovery investigation (research-focused).
3) Exploitation Phase — validate impact (controlled)
Simulate realistic attacker actions to measure real-world risk — always in a safe test environment.
Remote code execution attempts (simulated).
Privilege escalation testing to see how far access can be extended.
Lateral movement simulation inside the environment.
Data exfiltration validation to confirm the value of what an attacker could take.
4) Defense Evasion Testing — test detection & response
Make sure your controls don’t just exist — they actually catch and stop evasive techniques.
Firewall bypass techniques (testing allowed rules and gaps).
IDS/IPS evasion methods to verify detection coverage.
Antivirus/endpoint resilience checks (non-destructive).
Logging & monitoring avoidance tests to find blind spots.
Indonesian E-commerce Specifics:
Payment Gateway Security: Protecting Rupiah transactions worth billions daily
Customer Data Protection: Safeguarding 270+ million Indonesian digital consumers
Mobile-First Reality: 80% of Indonesian internet users are mobile-only
Cross-Border Compliance: Meeting both local and international regulations
Social Engineering Testing: The Human Firewall Challenge
Why This Is Critical for Indonesian Businesses:
Indonesian companies face over 4,000 phishing incidents annually, with attackers specifically targeting cultural and business contexts unique to Indonesia.
Testing Components:
Social Engineering Attack Simulation
Email Phishing Campaigns
Spear phishing using gathered employee intelligence
Business email compromise (CEO impersonation)
Credential harvesting with fake login pages
Malware delivery through document attachments
Voice Phishing (Vishing) Attacks
IT support impersonation calls
Bank representative fraud attempts
Government authority impersonation
Emergency scenario manipulation
Physical Security Testing
Tailgating into secure areas
Badge cloning and access card duplication
USB device drops in parking areas
Dumpster diving for sensitive documents
Social Media Intelligence Gathering
Employee profiling through LinkedIn/Facebook
Corporate information harvesting
Relationship mapping for targeted attacks
Organizational chart reconstruction
Indonesian Cultural Considerations:
Authority Respect: Attackers exploit hierarchical business culture
Religious Contexts: Phishing campaigns during Ramadan, Hari Raya
Language Mixing: Indonesian/English mixing creates translation vulnerabilities
Family Orientation: Attackers research employee families for leverage
Industrial Control System (ICS/SCADA) Testing: Critical for East Java
Essential for Manufacturing Corridor:
The East Java industrial belt faces unique challenges with Operational Technology (OT) security:
Testing Focus Areas:
Industrial Security Assessment
Human Machine Interface (HMI) Security
Operator workstation vulnerabilities
Authentication bypass techniques
Display manipulation attacks
Remote access security validation
Programmable Logic Controller (PLC) Testing
Firmware vulnerability analysis
Logic bomb insertion testing
Safety interlock bypass attempts
Production parameter manipulation
Network Protocol Security Assessment
Modbus protocol exploitation
DNP3 authentication weaknesses
Ethernet/IP security validation
Wireless industrial network testing
Safety System Integrity Verification
Emergency shutdown system testing
Alarm system manipulation detection
Safety instrumented system validation
Process safety barrier assessment
Regional Industry Impact:
Manufacturing Dominance: East Java produces 31% of Indonesia’s industrial output
Supply Chain Connectivity: Gresik chemicals → Sidoarjo manufacturing → Surabaya logistics
Economic Multiplier: One compromised facility affects 20+ downstream businesses
National Security: Critical infrastructure protection requirements
Looking for industry-specific testing tailored to your business? Contact JCSS Indonesia’s specialized testing teams.
Phase 1: Emergency Triage (Complete in 48 Hours)
Hour 1-4: The Security Reality Check
List all internet-connected systems
Identify customer data storage locations
Map critical business applications
Document third-party system connections
Count total user accounts (employees, contractors, vendors)
Identify privileged/admin account holders
Check for inactive/forgotten accounts
Review password policies and compliance
Run basic network port scans
Check for default passwords on devices
Identify unpatched systems
Test external website security basics
Confirm backup systems work
Test communication channels
Identify emergency contact procedures
Verify cybersecurity insurance coverage
Hour 4-24: Emergency Hardening
Multi-Factor Authentication: Enable on ALL business-critical accounts immediately
Password Overhaul: Change every default, weak, or shared password
Patch Blitz: Apply all critical security updates across systems
Access Lockdown: Disable unnecessary user accounts and privileges
Network Segmentation: Isolate critical systems from general network traffic
Hour 24-48: Professional Help Activation
Security Expert Engagement: Contact JCSS Indonesia for emergency consultation
Incident Response Plan: Develop basic breach response procedures
Staff Alert: Brief all employees on heightened security awareness
Communication Plan: Establish security incident escalation procedures
Documentation Start: Begin security inventory and policy documentation
Phase 2: Professional Defense Implementation (30-90 Days)
Days 1-14: Expert Assessment
Define scope and establish Rules of Engagement
Select appropriate testing methodology
Conduct business impact assessment
Create and align on a stakeholder communication plan
Perform external network penetration testing
Simulate internal lateral movement within the network
Conduct web application security assessments
Execute social engineering attack simulations
Evaluate physical security controls
Verify vulnerabilities and eliminate false positives
Provide business impact analysis with risk scoring
Deliver detailed technical documentation with proof-of-concept (PoC)
Summarize findings in an executive report with investment recommendations
Prioritize vulnerabilities using a risk-based approach
Identify cost-effective security solutions
Develop an implementation timeline
Define success metrics to measure improvements
Days 15-60: Critical Vulnerability Remediation
Emergency Fixes: Address all critical (9.0-10.0 CVSS) vulnerabilities immediately
High-Risk Mitigation: Implement compensating controls for complex vulnerabilities
System Hardening: Apply security configuration standards across infrastructure
Process Integration: Build security reviews into change management procedures
Monitoring Enhancement: Deploy security monitoring and alerting systems
Days 60-90: Strategic Security Enhancement
Advanced Controls: Deploy next-generation security technologies
Staff Training: Comprehensive cybersecurity awareness education
Vendor Security: Implement third-party security requirement programs
Compliance Framework: Establish regulatory compliance management system
Continuous Monitoring: Implement ongoing vulnerability management processes
Phase 3: Security Excellence Achievement (Ongoing)
The Continuous Protection Model:
Annual comprehensive penetration testing
Quarterly focused security assessments
Monthly vulnerability scanning
Weekly security metrics review
Red team exercises simulating nation-state attacks
Purple team collaborative defense improvement
Tabletop exercises for crisis management
Business continuity and disaster recovery testing
Security metrics dashboard for leadership
Vulnerability reduction tracking
Incident response time measurement
Compliance status monitoring
Emerging threat research and preparation
New technology security integration
Industry best practice adoption
Security culture development and maintenance
🏦 Financial Services: Fort Knox-Level Defense
The Multi-Layer Defense Architecture:
Web Application Firewall (WAF) with AI threat detection
DDoS protection capable of handling 100+ Gbps attacks
Bot management platform filtering automated attacks
Real-time transaction fraud detection with ML algorithms
Customer authentication with biometric verification
Database encryption with hardware security modules (HSMs)
Application-level encryption for all sensitive data
Secure coding practices with automated security testing
Real-time fraud detection with behavioral analysis
Privileged access management with session recording
Zero-trust network access with device verification
Email security gateway with advanced threat protection
Endpoint detection and response (EDR) on all devices
Security awareness training with phishing simulation
Insider threat monitoring with user behavior analytics
API security gateway with rate limiting and authentication
Vendor risk assessment with continuous monitoring
Secure file transfer with end-to-end encryption
Supply chain security monitoring with threat intelligence
Manufacturing: Operational Technology Security
The OT/IT Convergence Challenge:
Air-gapped OT networks with secure data diodes
Industrial DMZ for controlled OT/IT communication
VLAN segmentation by production line and function
Micro-segmentation for critical control systems
PLC security hardening with firmware integrity checking
HMI access controls with role-based permissions
SCADA system monitoring with anomaly detection
Safety system integrity validation with continuous monitoring
Modbus protocol security with authentication and encryption
DNP3 secure authentication implementation
Ethernet/IP security with network access control
Wireless industrial network security with WPA3-Enterprise
Industrial facility access control with biometric verification
CCTV monitoring with AI-powered threat detection
Environmental monitoring for tampering detection
Maintenance access logging with contractor verification
E-commerce: Customer Data Fortress
The Customer Trust Security Model:
OWASP Top 10 vulnerability prevention with code review
Input validation frameworks preventing injection attacks
Session management security with secure cookie implementation
API security with OAuth 2.0 and rate limiting
Content Security Policy (CSP) preventing XSS attacks
PCI DSS Level 1 compliance with annual validation
Tokenization implementation for credit card data
Fraud detection systems powered by machine learning
Secure payment gateways with end-to-end encryption
Mobile payment security with app attestation
Personal data encryption using AES-256
Privacy control implementation with consent management
Data minimization practices to reduce exposure
Right to erasure automation for GDPR compliance
Data breach response plan with 72-hour notification
Multi-cloud security configuration management
Container security with runtime protection
CDN security optimization with DDoS protection
Backup and recovery with immutable storage
Infrastructure as code (IaC) security scanning
While you’ve been reading this guide, here’s what’s happened to Indonesian businesses:
⏰ In the last 30 minutes:
68 cyberattacks have targeted Indonesian organizations
15 businesses have discovered they’re already compromised
3 companies have received ransom demands
1 business has permanently closed due to a cyberattack
📊 The Waiting Game Statistics:
287 days: Average time hackers spend in networks before detection
24 hours: Typical ransomware deployment time after initial compromise
60%: Small businesses that close permanently within 6 months of a breach
11%: Indonesian organizations with mature cybersecurity (are you one?)
Future 1: The Ostrich Path (Do Nothing)
12 months from now…
You’re still reading cybersecurity articles, still “planning to do something soon,” still hoping it won’t happen to you. Then one Monday morning, your employees can’t log in. Your systems are encrypted. Your customer data is for sale on the dark web. Local news is reporting your breach. Your business bank account is frozen. Your biggest clients are terminating contracts.
The Statistics Don’t Lie:
85% probability of a successful cyberattack within 2 years
₹15+ billion average cost of a major breach
60% chance your business won’t survive 6 months post-breach
5-10 years to rebuild reputation and customer trust
Future 2: The DIY Hero Path (Wing It Yourself)
12 months from now…
You’ve installed some security software, changed some passwords, maybe even hired an IT person. You feel safer, but you’re operating on hope, not knowledge. You don’t know what you don’t know. Your “security” has gaps you can’t see, and criminals are experts at finding and exploiting exactly those blind spots.
The Reality Check:
40% probability of successful attack due to unknown vulnerabilities
₹8+ billion average cost when amateur security fails
False sense of security often worse than no security
Compliance failures leading to regulatory penalties
Future 3: The Professional Partnership Path (JCSS Indonesia)
12 months from now…
You sleep peacefully knowing exactly where your vulnerabilities were, because you found and fixed them before criminals could. Your employees are security-aware and vigilant. Your customers trust you with their data. Regulators see you as a compliance leader. You’re protected, prepared, and profitable.
The Professional Advantage:
85% reduction in successful attack probability
300%+ ROI on cybersecurity investment
Regulatory compliance protecting against penalties
Customer trust driving business growth
Competitive advantage winning security-conscious clients
Proven Track Record That Speaks Volumes:
10+ years protecting Indonesian businesses across every sector
200+ successful security transformations delivered
Zero data breaches during any testing engagement (perfect security record)
98% client satisfaction with consistently exceeded expectations
National recognition as Indonesia’s leading cybersecurity consulting firm
Technical Excellence That Criminals Fear:
International certifications: CREST, CEH, OSCP qualified professionals
Advanced methodologies: Cutting-edge tools and techniques
Industry specialization: Deep expertise in financial, manufacturing, government, technology
Innovation leadership: Continuous R&D in cybersecurity advancement
Local adaptation: Global standards customized for Indonesian business environment
🇮🇩 Indonesian Market Leadership That Regulators Respect:
Regulatory mastery: Complete understanding of UU PDP, OJK requirements, upcoming RUU KKS
Cultural fluency: Indonesian business practices and communication preferences
Government relations: Trusted advisor to public and private sector leaders
Local presence: Jakarta headquarters with nationwide service coverage
Industry networks: Strong relationships across Indonesian business ecosystem

Step 1: FREE Security Consultation (Next 24 Hours)
Don’t spend another sleepless night wondering about your vulnerabilities. Get immediate clarity on your security posture with JCSS Indonesia’s complimentary assessment consultation.
What You Get:
30-minute expert consultation with certified cybersecurity professionals
Risk assessment overview identifying your highest-priority concerns
Customized recommendations specific to your business and industry
Transparent cost estimates with no hidden fees or pressure tactics
Clear next steps whether you’re ready now or need time to plan
Step 2: Professional Penetration Testing (Next 30 Days)
Stop guessing about your security and start knowing exactly where you stand. JCSS Indonesia’s comprehensive penetration testing reveals every vulnerability before criminals find them.
What You Receive:
Certified ethical hackers using real criminal techniques safely
Comprehensive assessment of networks, applications, and human factors
Detailed findings with proof-of-concept demonstrations
Executive summary for leadership decision-making
Step-by-step remediation guide for every discovered vulnerability
Step 3: Complete Security Transformation (Next 90 Days)
Don’t just fix problems—build lasting protection that grows with your business. Partner with JCSS Indonesia for comprehensive security program development.
Your Partnership Benefits:
Implementation support through every security improvement
Ongoing consultation for strategic security decisions
Regular retesting to verify continued protection
Compliance management keeping you ahead of regulatory changes
24/7 emergency support when you need us most
Stop Reading. Start Protecting.
Every minute you spend thinking about cybersecurity instead of implementing it is another minute criminals have to study your systems and plan their attack. The choice is simple: Professional protection or criminal prosecution.
Your Direct Line to Bulletproof Cybersecurity:
Contact JCSS Indonesia NOW:
📧 Email: [email protected]
☎️ Phone: +62 21 3882 5222
🏢 Address:Graha Casablanca 45 JL. Raya Casablanca No.45, Level 3 Tebet, Jakarta 12960,
Indonesia.🌐 Instant Consultation: Schedule Your Free Security Assessment
What Happens When You Contact Us RIGHT NOW:
Immediate Response (Within 4 Hours):
Personal consultation with certified cybersecurity expert
Quick assessment of your most urgent security concerns
Emergency recommendations you can implement today
Transparent discussion of testing options and investment
Detailed Proposal (Within 48 Hours):
Customized penetration testing methodology for your business
Transparent pricing with no hidden fees or surprises
Realistic timeline with minimal business disruption planning
Clear deliverables and success metrics
Professional Security Testing (Within 2 Weeks):
CREST-certified ethical hackers begin comprehensive assessment
Daily communication and immediate critical issue alerts
Evidence-based vulnerability documentation with business impact
Executive briefing with strategic security recommendations
When you choose JCSS Indonesia, you’re not buying a service—you’re investing in a partnership that will protect your business, your customers, and your future for years to come.
Our Commitment to Your Security Success:
Quality guarantee: Professional, thorough testing with actionable results
Partnership approach: Long-term relationship focused on your security evolution
Transparency promise: Clear communication and honest recommendations
Success measurement: Quantifiable improvement in your security posture
Ongoing support: Your trusted cybersecurity advisor through every challenge
Your Bulletproof Future Starts With ONE Decision
Five years from now, when cyberattacks have become even more devastating, when regulatory penalties have increased, when customer expectations for data protection have reached new heights—you’ll look back at this moment as the turning point.
The moment you stopped being a potential victim and became a protected professional organization.
The moment you chose investment over gambling, preparation over hope, partnership over isolation.
The moment you chose JCSS Indonesia to build your bulletproof cybersecurity future.
Contact JCSS Indonesia RIGHT NOW – Secure Your Free Consultation
Your business is worth protecting. Your customers deserve security. Your future depends on the decision you make in the next 5 minutes.
Don’t let cybercriminals write your business obituary. Choose JCSS Indonesia. Choose professional protection. Choose to survive and thrive.
🔒 SECURE YOUR BUSINESS. SECURE YOUR FUTURE. CONTACT JCSS INDONESIA TODAY. 🔒
📞 +62 21 3882 5222
📧 [email protected]
🌐 Get Your FREE Cybersecurity Consultation Now
The clock is ticking. Your protection is waiting. Make the call that saves your business.

Comments are closed.

love language test is a quick quiz for couples to discover their love languages and strengthen their connection through better understanding and communication.