Table of Contents
ToggleInsights, Lessons, and Strategies for Securing Your Business in an Unforgiving Digital Landscape
In today’s interconnected world, the specter of data breaches looms large, threatening the very foundation of trust and security in the digital realm. As technology advances, so do the tactics of malicious actors, leaving no industry untouched by the menace of cyber threats. In this article, we delve deep into the recent high-profile data breaches of 2023, shedding light on the vulnerabilities exposed and offering valuable insights to safeguard your organization. Prepare to be informed, motivated, and empowered as we navigate through the storm of data breaches together.
Understanding the Landscape of Recent Data Breaches
As the digital landscape evolves, so do the methods employed by cybercriminals to infiltrate systems and extract sensitive information. In this section, we explore the major data breaches that have rocked the corporate world in 2023, highlighting the key lessons learned and the potential consequences faced by organizations and individuals alike.
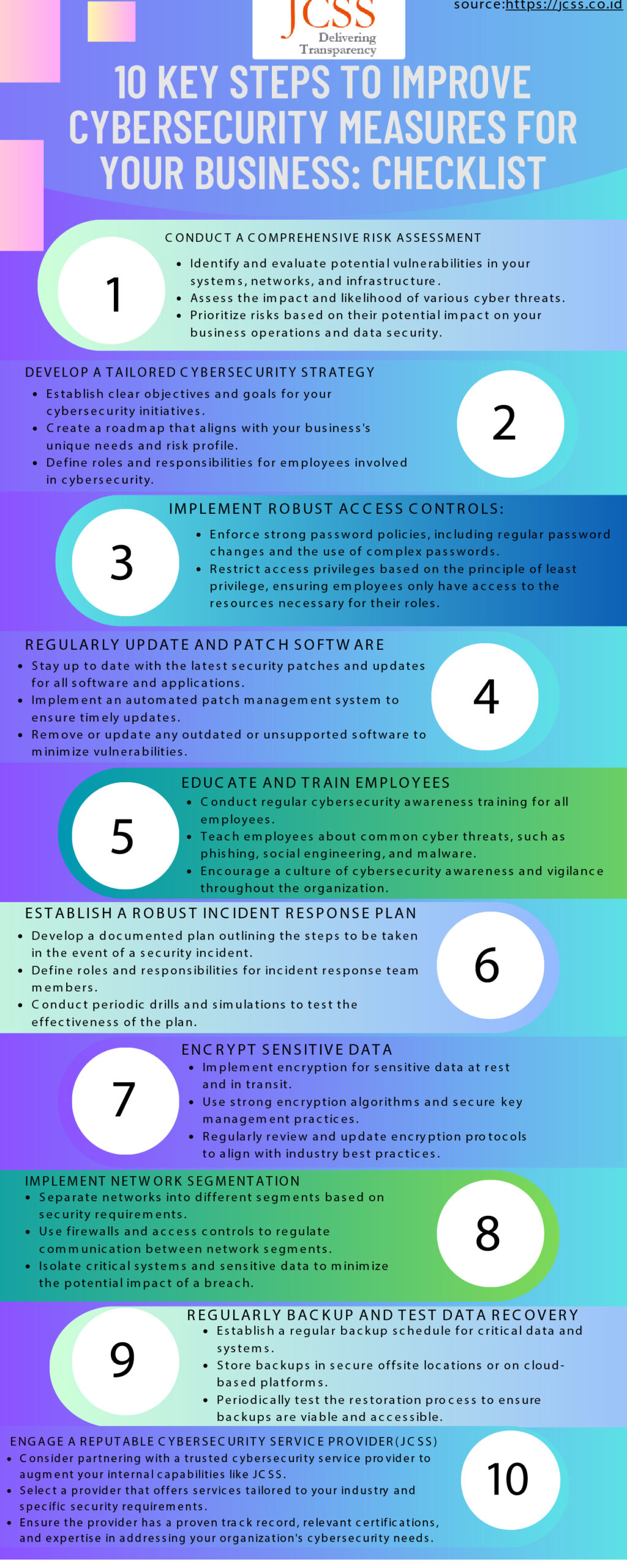
Here is a checklist of 10 Key Steps to Improve Cybersecurity Measures for Businesses
#Step 1 Conduct a Comprehensive Risk Assessment:
- Identify and evaluate potential vulnerabilities in your systems, networks, and infrastructure.
- Assess the impact and likelihood of various cyber threats.
- Prioritize risks based on their potential impact on your business operations and data security.
#Step 2 Develop a Tailored Cybersecurity Strategy:
- Establish clear objectives and goals for your cybersecurity initiatives.
- Create a roadmap that aligns with your business’s unique needs and risk profile.
- Define roles and responsibilities for employees involved in cybersecurity.
#Step 3 Implement Robust Access Controls:
- Enforce strong password policies, including regular password changes and the use of complex passwords.
- Implement multi-factor authentication (MFA) for all critical systems and accounts.
- Restrict access privileges based on the principle of least privilege, ensuring employees only have access to the resources necessary for their roles.
#Step 4 Regularly Update and Patch Software:
- Stay up to date with the latest security patches and updates for all software and applications.
- Implement an automated patch management system to ensure timely updates.
- Remove or update any outdated or unsupported software to minimize vulnerabilities.
#Step 5 Educate and Train Employees:
- Conduct regular cybersecurity awareness training for all employees.
- Teach employees about common cyber threats, such as phishing, social engineering, and malware.
- Encourage a culture of cybersecurity awareness and vigilance throughout the organization.
#Step 6 Establish a Robust Incident Response Plan:
- Develop a documented plan outlining the steps to be taken in the event of a security incident.
- Define roles and responsibilities for incident response team members.
- Conduct periodic drills and simulations to test the effectiveness of the plan.
#Step 7 Encrypt Sensitive Data:
- Implement encryption for sensitive data at rest and in transit.
- Use strong encryption algorithms and secure key management practices.
- Regularly review and update encryption protocols to align with industry best practices.
#Step 8 Implement Network Segmentation:
- Separate networks into different segments based on security requirements.
- Use firewalls and access controls to regulate communication between network segments.
- Isolate critical systems and sensitive data to minimize the potential impact of a breach.
#Step 9 Regularly Backup and Test Data Recovery:
- Establish a regular backup schedule for critical data and systems.
- Store backups in secure offsite locations or on cloud-based platforms.
- Periodically test the restoration process to ensure backups are viable and accessible.
#Step 10 Engage a Reputable Cybersecurity Service Provider:
- Consider partnering with a trusted cybersecurity service provider like JCSS Global to augment your internal capabilities.
- Select a provider that offers services tailored to your industry and specific security requirements. We offer tailored security requirements for your business at affordable rates with expert guidance at each and every step.
- Ensure the provider has a proven track record, relevant certifications, and expertise in addressing your organization’s cybersecurity needs. Get a free site Security audit fill a form and let our experts guide you to cybersecurity enlightenment.
Remember, cybersecurity is an ongoing effort that requires continuous monitoring, adaptation, and improvement. By following this checklist and regularly reviewing and updating your security measures, you can enhance your organization’s resilience against cyber threats and protect your valuable assets.
Top 8 Recent High-Profile Company Data Breaches in 2023
1. T-Mobile: May 2023 (and January 2023)
2. Yum Brands (KFC, Taco Bell, & Pizza Hut): April 2023
3. ChatGPT: March 2023
4. Chick-fil-A: March 2023
5. Activision: February 2023
6. Google Fi: February 2023
7. MailChimp: January 2023
Read More: Penasihat Risiko
Read More: Otomasi GRC
Read More: Cyber Assurance & ISA
8. Norton Life Lock: January 2023
Companies with the Most Data Breaches in 2023
- Old vulnerabilities: It’s not uncommon for a hacker to leave a secret window that they can use to access a company’s systems again after a successful first attempt. Failing to patch these vulnerabilities can lead to a second attack.
- Human error: Employees using weak passwords may expose a company’s systems to subsequent attacks. Other common human errors include employees clicking on malicious links and visiting phishing sites. Unless you perform follow-up security training following an initial breach, employees can repeat previous mistakes that leave your business vulnerable.
- Malware: Hackers use malicious software such as viruses, ransomware, Trojans, spyware, adware, etc., to steal confidential information from an organization’s network system. If a company fails to step up monitoring protocols after its first breach, there is nothing to stop repeat attacks from occurring.
The Path to a Secure Future
Crafting a Comprehensive Cybersecurity Strategy
Safeguard Your Company Today
Conclusion
The world of cybersecurity is ever evolving, and recent high-profile data breaches serve as reminders of the importance of remaining vigilant. In this article, we have explored the landscape of data breaches, learned from real-world case studies, and provided strategies to strengthen your organization’s cybersecurity defenses. By taking a proactive stance, partnering with reputable service providers, and staying informed, you can navigate the storm of data breaches with confidence. The time to act is now, as we pave the way towards a secure and resilient digital future.
Contact Us Now to schedule a free consultation and take the first step towards a more secure business.


