In today’s world, where everything is online, cybersecurity has become a major concern. Cyber-attacks are increasing everyday, and it’s important to know how to identify them to protect yourself. Here are 10 ways to identify a cyber-attack and how to protect yourself with examples.
Table of Contents
ToggleTable of Contents
- Introduction
- What is a Cyber Attack?
- Types of Cyber Attacks
- Phishing
- Malware
- Denial-of-Service (DoS) attacks
- Man-in-the-Middle (MITM) attacks
- Signs of a Cyber Attack
- How to Protect Yourself from Cyber Attacks
- Use Strong Passwords
- Keep Your Software Up-to-Date
- Use Two-Factor Authentication
- Backup Your Data
- Install Anti-virus Software
- What to Do If You Are a Victim of a Cyber Attack?
- Examples of Cyber Attacks
- WannaCry Ransomware Attack
- Target Data Breach
- Equifax Data Breach
- Conclusion
- FAQs
- What is a Cyber Attack?
- What are the types of Cyber Attacks?
- How can you identify a Cyber Attack?
- How to protect yourself from a Cyber Attack?
- What should you do if you are a victim of a Cyber Attack?
Introduction
In recent years, we have seen an increase in the number of cyber-attacks. Cyber criminals are using sophisticated methods to steal personal information, financial data, and even corporate secrets. Therefore, it is crucial to know how to identify a cyber-attack and how to protect yourself from it.
Below are few statistics of cyber trends in cybersecurity:
- According to a Deloitte Center for Controllership poll. “During the past 12 months, 34.5% of polled executives report that their organizations’ accounting and financial data were targeted by cyber adversaries.
- Within that group, 22% experienced at least one such cyber event and 12.5% experienced more than one.” And “nearly half (48.8%) of C-suite and other executives expect the number and size of cyber events targeting their organizations’ accounting and financial data to increase in the year ahead.
- And yet just 20.3% of those polled say their organizations’ accounting and finance teams work closely and consistently with their peers in cybersecurity.”
- Perhaps no cybersecurity trend has been bigger in the last several years than the scourge of attacks related to the supply chain. Cyber incidents, such as the breach at software management vendor SolarWinds and Log4j in the open-source world, put organizations around the globe at risk. Analyst firm Gartner predicted that by 2025, 45% of global organizations will be impacted in some way by a supply chain attack.
- The volume of reported vulnerabilities continues to rise. The HackerOne 2022 “Hacker-Powered Security Report” found that ethical hackers were able to discover over 65,000 vulnerabilities in 2022 alone, up by 21% over 2021.
- Cybersecurity measures in place by businesses, governments and individuals are increasingly being rendered obsolete by the growing sophistication of cybercriminals, according to “The Global Risks Report 2022” from the World Economic Forum.
- The cost of cybercrime is predicted to hit $8 trillion in 2023 and will grow to $10.5 trillion by 2025, according to Cybersecurity Ventures’ “2022 Official Cybercrime Report,” sponsored by eSentire.
- While businesses try to protect their own sensitive files from attack, customer information is stored in vulnerable databases all over the world. Identity fraud losses tallied a total of $52 billion and affected 42 million U.S. adults, according to “2022 Identity Fraud Study: The Virtual Battleground” From Javelin Strategy & Research.
- It takes an average of 277 days for security teams to identify and contain a data breach, according to “Cost of a Data Breach 2022,” a report released by IBM and Ponemon Institute.
- Cryptojacking is incredibly prevalent, growing by 230% in 2022, according to Kaspersky Lab.
- The same study noted that most hackers earn variable amounts from crypto jacking, with an average of approximately $1,600 per month.
- According to the IBM “Cost of a Data Breach 2022” report, data breaches involving lost or stolen credentials take longer to identify and cost $150,000 more than the average data breach.
The FBI’s Internet Crime Complaint Center reported the volume of complaints in 2021 as 847,376, an all-time high. Total losses from those complaints totaled over $6.9 billion.
What is a Cyber Attack?
A cyber-attack is an attempt by cyber criminals to gain unauthorized access to computer systems, networks, or devices. The main goal of a cyber-attack is to steal, modify or destroy sensitive data, disrupt normal business operations, or extort money from the victims.
Types of Cyber Attacks
Phishing
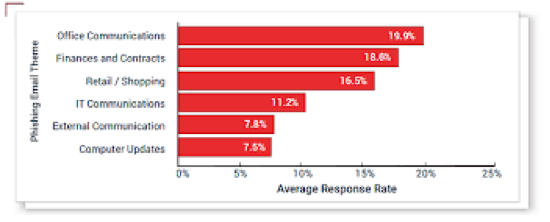
Phishing is a type of cyber-attack in which cyber criminals use fake emails or websites to trick individuals into revealing sensitive information such as login credentials, credit card numbers, or personal details.
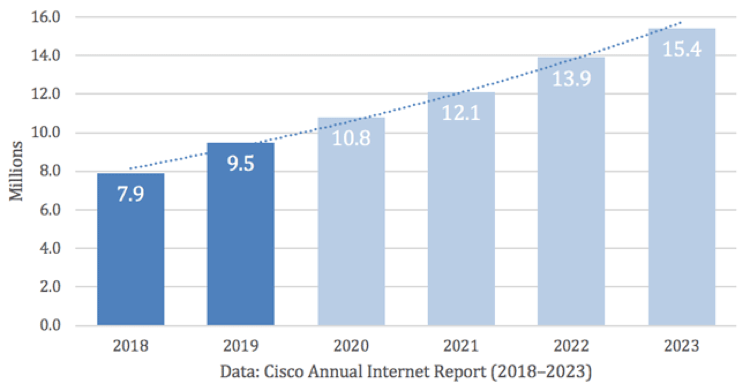
Below is a chart that shows average weekly cyber-attacks per organization 2022 compared to 2021.
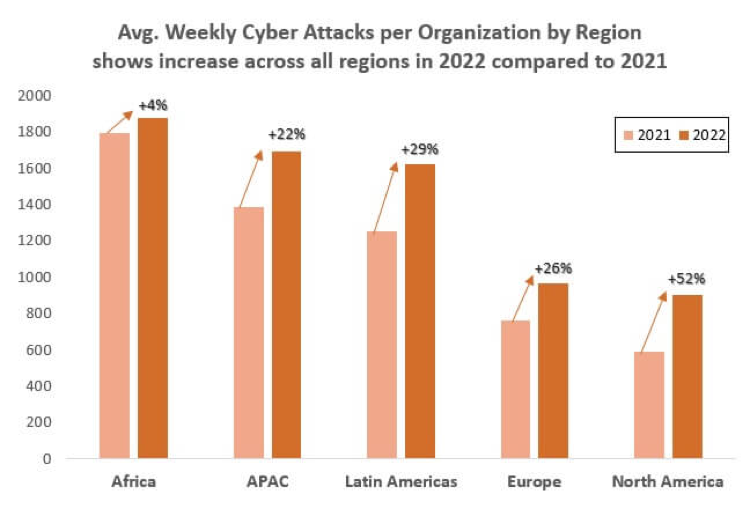
Source: Checkpoint Research
Read More: Risk And Compliance Ultimate Guide: How To Manage Your Operations, Risks, And Compliance Obligations Effectively
Read More: A Complete Guide To GRC Automation And Enterprise Risk Management
Malware
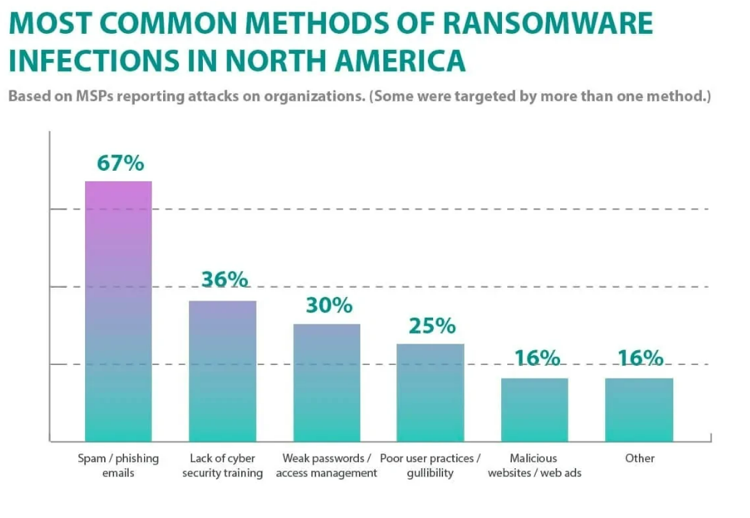
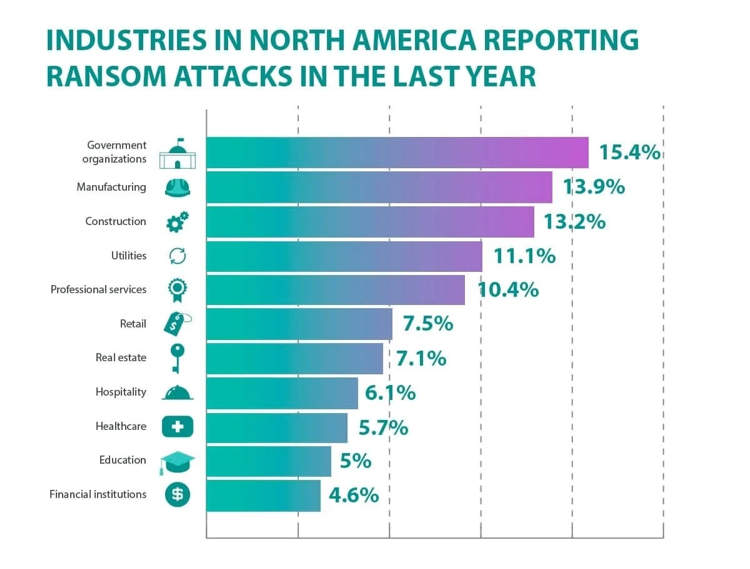
Source: https://www.safetydetectives.com/blog/ransomware-statistics/
Above you can see the most common methods of ransomware infections in north america.
Malware is a type of software that is designed to harm computer systems, networks, or devices.
Malware can infect a computer through email attachments, infected websites, or infected software downloads.
Once installed, malware can steal sensitive information, destroy files, or even take control of the computer.
Denial-of-Service (DoS) attacks
A denial-of-service (DoS) attack is a cyber-attack in which cyber criminals overwhelm a website or network with a flood of traffic, making it unavailable to users.
The goal of a DoS attack is to disrupt normal business operations, extort money, or cause reputational damage.
Man-in-the-Middle (MITM) attacks
- Signs of a Cyber Attack
- Here are some signs that you may be a victim of a cyber-attack:
- Unusual computer behavior
- Pop-up ads or unwanted toolbars
- Slow computer performance
- Unexplained changes to files or settings
- Unusual network activity
Read More: Otomasi GRC
Read More: Cyber Assurance & ISA
How to Protect Yourself from Cyber Attacks
Prevention is better than cure, and the same applies to cybersecurity. Here are some ways to protect yourself from cyber-attacks:
Use Strong Passwords
“Cybercriminals are always finding new ways to attack individuals and businesses, but by taking a few simple steps such as using strong passwords and keeping software up-to-date, you can significantly reduce your risk of falling victim to an attack.” – Ciaran Martin, former CEO of the UK’s National Cyber Security Centre.
Using strong passwords is one of the most basic ways to protect yourself from cyber-attacks. A strong password should be at least 8 characters long and should include a mix of upper and lowercase letters, numbers, and symbols. It’s also important to use different passwords for different accounts.
Keep Your Software Up-to-Date
“One of the most effective ways to protect yourself from cyber-attacks is to be aware of the threats and understand how they work. This means staying up-to-date with the latest security news and being able to recognize suspicious activity on your devices.” – David Emm, Principal Security Researcher at Kaspersky.
Keeping your software up-to-date is crucial in protecting yourself from cyber-attacks. Software updates often include security patches that address vulnerabilities that cyber criminals may exploit.
You should regularly check for software updates and install them as soon as possible.
Use Two-Factor Authentication
“Two-factor authentication is one of the most important security measures you can use to protect your online accounts. By requiring a second form of identification, such as a code sent to your phone, you can significantly reduce the risk of an attacker gaining access to your account.” – Alex Heid, Chief Research Officer at SecurityScorecard.
Two-factor authentication adds an extra layer of security to your accounts. It requires you to provide two forms of identification to access your accounts, such as a password and a code sent to your phone. Many online services, including email and social media accounts, offer two-factor authentication.
Backup Your Data
“Regularly backing up your data is essential for protecting yourself against ransomware attacks. If you have a recent backup, you can restore your files without having to pay the ransom.” – Brian Krebs, Investigative Journalist and Cybersecurity Expert.
Backing up your data is an important step in protecting yourself from cyber-attacks. If your computer is infected with malware, you may lose all your data.
By backing up your data regularly, you can ensure that you don’t lose anything important.
Install Anti-virus Software
“It’s important to remember that cyber-attacks can happen to anyone, so it’s essential to have a plan in place in case the worst happens. This includes knowing how to report a cyber-attack and having a plan for recovering your data.” – Raj Samani, Chief Scientist and Fellow at McAfee.
Installing anti-virus software is another basic step to protect yourself from cyber-attacks. Anti-virus software can detect and remove malware from your computer.
You should regularly update your anti-virus software to ensure that it can detect the latest threats.
What to Do If You Are a Victim of a Cyber Attack?
If you are a victim of a cyber-attack, you should take the following steps:
- Disconnect from the Internet
- Change your passwords
- Contact your bank or credit card company
- Report the incident to the authorities
- Consider getting professional help
- Examples of Cyber Attacks
Here are some examples of high-profile cyber-attacks:
WannaCry Ransomware Attack
The WannaCry ransomware attack occurred in May 2017 and infected more than 200,000 computers in 150 countries. The attack encrypted the victims’ files and demanded a ransom to be paid in Bitcoin.
Target Data Breach
In December 2013, Target suffered a massive data breach that affected up to 110 million customers. The breach was caused by a vulnerability in Target’s payment system that allowed cyber criminals to steal credit and debit card information.
Equifax Data Breach
In 2017, Equifax, one of the largest credit reporting agencies in the US, suffered a data breach that exposed the personal information of up to 143 million customers. The breach was caused by a vulnerability in Equifax’s web application software.
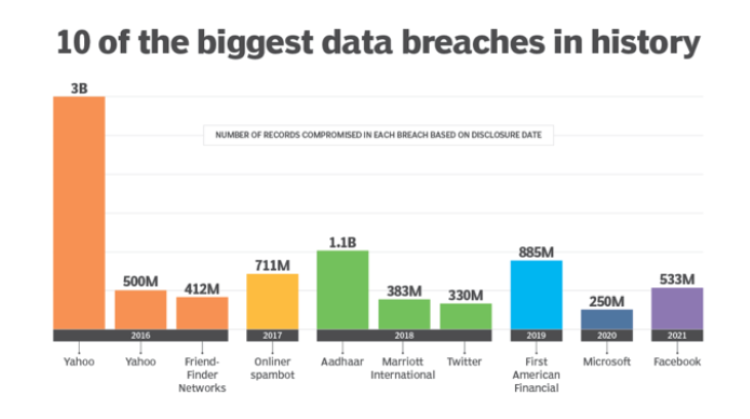
Below are 10 of the biggest data breaches in history.
Conclusion
In conclusion, cyber-attacks are becoming more common, and it’s important to know how to protect yourself. By following the tips outlined in this article, you can reduce the risk of becoming a victim of a cyber-attack. Remember to stay vigilant and take the necessary steps to protect yourself and your data.
How we can help
At JCSS in Indonesia, we help you rethink risk and compliances, develop strategies and enhance value, opening the doors to vast opportunities. JCSS has been rendering advice to over 450 clients spread across a broad spectrum of industries ranging from Infrastructure to Manufacturing, Construction to Information Technology. Our portfolio of clients ranges from starting companies in India, Indonesia, Japan & Singapore.

