Nowadays, keeping data safe is key. Customers expect groups to put measures in place that guard private information.
If standards are not met, an organization’s reputation and money can take a big hit.
That’s why SOC 2 compliance matters. SOC 2 reports show service organizations have necessary controls for security, access, data processing, privacy and confidentiality according to Trust Services Criteria (TSC).
CPAs (auditors) check if organizations meet strict requirements made by the AICPA.
This article looks closely at key SOC 2 compliance requirements groups need to achieve. We’ll explore criteria around security, access, processing, privacy and confidentiality.
Understanding SOC 2 helps pick trustworthy partners and avoid data breaches. Let’s review the main points.
Understanding SOC 2 Compliance: Unveiling the Basics
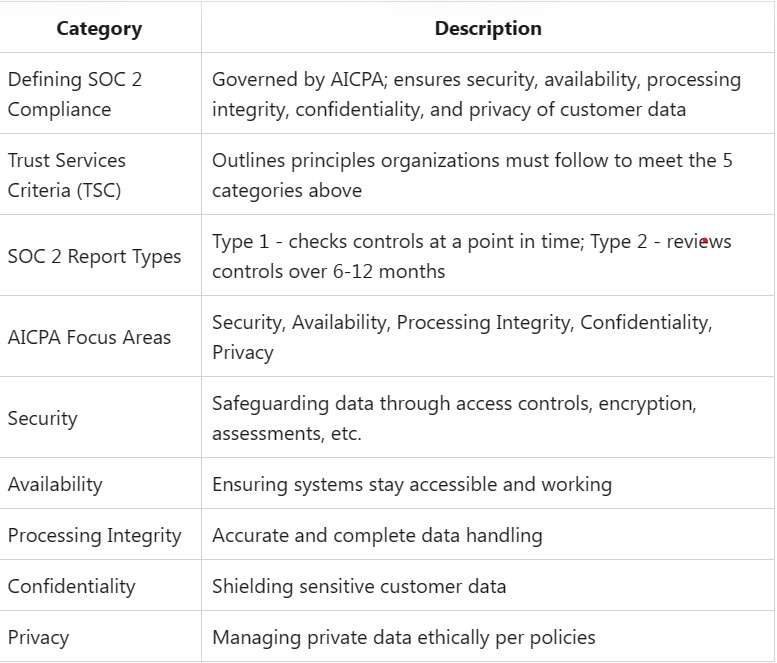
Defining SOC 2 Compliance
SOC 2 compliance, governed by the American Institute of Certified Public Accountants (AICPA), is a framework designed to ensure the security, availability, processing integrity, confidentiality, and privacy of customer data.
Trust Services Criteria (TSC)
An integral part of SOC 2 compliance, TSC outlines the principles that organizations must follow to meet the five criteria mentioned above. We explore these criteria in detail, emphasizing their role in securing customer trust.
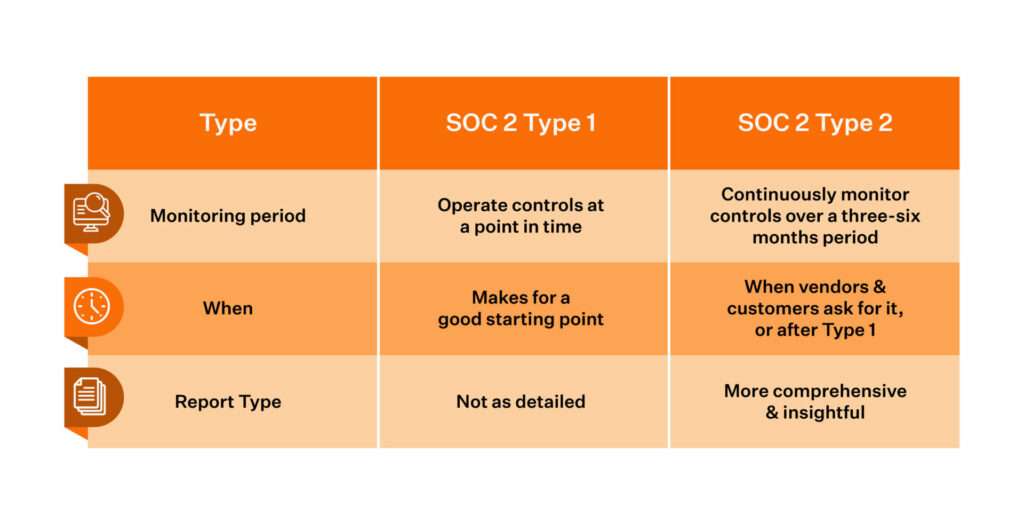
SOC 2 Reports: Type I vs. Type II
SOC 2 reports formally say tech suppliers protect customer data infrastructure. There are two report types:
SOC 2 Type 1 – Checks if an organization’s controls meet AICPA standards at a certain time. Good for showing security to possible customers.
SOC 2 Type 2 – Reviews controls over 6-12 months. Makes sure safety measures stay solid over time.
AICPA Points of Focus
TSC outlines five main rules for SOC 2:
- Security – Safeguarding data using access controls, encryption, assessments, etc.
- Availability – Ensuring systems with customer data stay accessible and working.
- Processing Integrity – Handling data fully and precisely; tracking transactions.
- Confidentiality – Shielding sensitive customer data to stop unauthorized access.
- Privacy – Managing private data according to TSC criteria.
A SOC 2 report measures an organization against all five of these Trust Principles.
Strong proof is needed to show AICPA standard alignment before auditors give a formal thumbs-up. Now let’s explore key infrastructure and policies.
Read More: What Is Social Engineering: Types Of Attacks & How To Prevent
Security: Protecting Systems and Information
The security standard covers controls limiting unauthorized data access. Main requirements:
- Access Controls: Multi-factor sign-on, password rules, firewalls, anti-malware, intrusion monitoring, strict settings, encrypting data at rest and in motion.
- Physical Controls: ID systems to enter facilities; locked server rooms with tight access; security cameras.
- Operational Controls: Formal change procedures; vulnerability tests; penetration testing; labeling sensitive data; central logging and watching.
- Risk Management: Processes to ID, analyze and lower operational dangers threatening security. Includes vendor risk reviews.
- Security Program: Comprehensive rules on data retention, classification, use, incident response and recovery, security roles.
Infrastructure is one piece. Standards like NIST Cybersecurity Framework also guide policies, procedures, and design. As threats change, steady improvement keeps controls effective.
Availability: Delivering Reliable Access
Availability means systems providing customer access stay available and work per agreements. Key standards demand reliability and bounce-back ability by having:
- Redundant Infrastructure: Backup paths, load balancing, failover sites, clustered tiers to avoid downtime from part failure.
- Backup & Restore Testing: Regularly backing up customer data and testing restores.
- Capacity Monitoring: Watching system usage compared to baselines; adding resources to maintain performance per SLAs.
- Maintenance Windows: Changes follow strict procedures with downtime per SLAs.
Robust availability practices prevent denial attacks, outages and performance problems threatening uptime.
Read More: Take Your Business From Good To Great With An Internal Audit
Processing Integrity: Accurate, Complete Data Handling
Processing integrity means complete, valid transactions without manual workarounds or lost data. Main requirements:
- Data Validation Checks: Front-end and back-end processes confirm accuracy and completeness of transaction information.
- Transaction Logging: Detailed audit trails recording all system activity, with unique IDs.
- Data Integrity Testing: Comparing production subsets against test data to catch possible corruption.
- Capacity Planning: Watching usage and planning infrastructure to handle spikes without accuracy drops.
Such practices prevent failed transactions and errors weakening data reliability.
Confidentiality: Blocking Unapproved Access
Confidentiality stops unauthorized access and leaks through company-wide rules and access limits like:
- Least-Privilege Access: Only granting essential access to do jobs; removing when no longer needed.
- Encryption: Encrypting sensitive information per standards like AES-256.
- Data Classification: Labeling data sensitivity (public, internal, confidential); handling per policy.
- Personnel Screening: Stringent background checks; security awareness training.
- Data Loss Prevention: Network tools catching unauthorized export attempts.
Confidentiality reduces insider and partner data exposure threats.
Privacy: Keeping Data Handling Promises
Finally, privacy governs ethical personal data handling per published policies like:
- Privacy Policy: Public statement on what personal data is gathered, why, retention times, transfers.
- Consent: Checkboxes for transparent user control over data use.
- Data Minimization: Only collecting essential personal info to deliver service.
- Request/Complaint Processes: Easy ways to update information or raise handling concerns.
- Third-Party Assessments: Ensuring vendors handle personal data properly.
Such privacy practices comply with regulations like GDPR and build user trust that private details stay protected.
Achieving Continuous SOC 2 Conformance
While the above outlines key SOC 2 criteria, just having controls isn’t enough. Groups must prove to auditors that infrastructure, policies, and procedures demonstrably meet AICPA requirements over time.
Trends like cloud add complexity. When working with vendors handling sensitive data, SOC 2 reports confirm critical controls stay solid as threats change. No one is immune without steady compliance with leading standards.
What Are SOC 2 Compliance Requirements?
SOC 2 compliance requirements are the criteria an organization has to meet to earn its certification from an independent auditor. The Association of International Certified Professional Accountants (AICPA) has broken down SOC 2 compliance into five known as the Trust Services Criteria: security, availability, confidentiality, processing integrity, and privacy.
It’s important to note that the number of TSC requirements needed for SOC 2 certification is not uniform for all companies. Instead, what organizations have to do varies on a case-by-case basis due to factors like management and auditor discretion. That said, all organizations need to meet the security requirements to earn their SOC 2 certification.
Because it defines the industry standards, AICPA is the undisputed authority on SOC 2 compliance requirements. Visit AICPA’s blog to learn more about the TSC and other key compliance resources.
What Are the 5 Categories of SOC 2 Compliance Requirements?
Security Requirements
To meet the SOC 2 security criteria — also called “Common Criteria” (CC) — a company must demonstrate it can keep bad actors from compromising its data and tech stack. This capability is evaluated by auditors using a series of nine different CC requirements. Here are key questions that each of those requirements seeks to answer, along with the overall scope of each requirement.
- CC1.0: Has the company set up the control environment appropriately? These requirements cover company leadership formation, talent acquisition, and staff training.
- CC2.0: Does the company have the right data management practices? These controls concern how data is collected and shared.
- CC3.0: Does the company follow relevant risk assessment practices? These requirements often focus on financial and technical risks.
- CC4.0: Does the company have robust compliance monitoring capabilities? These requirements determine an organization’s internal evaluation and reporting processes.
- CC5.0: Can the company effectively execute compliance initiatives? These controls ensure that a company can adopt compliance measures across the organization and within its tech stack.
- CC6.0: How do the company’s compliance measures relate to its security capabilities? These requirements address data access, handling, and deletion practices.
- CC7.0: Does the company have the right systems and operational controls? These requirements focus on incident response capabilities.
- CC8.0: Can the company navigate change management? These controls ensure a company has the processes to handle organizational and policy shifts.
- CC9.0: Is the company taking the appropriate steps to mitigate risks? These requirements include activities addressing internal risks — as well as vendor and partner risks.
The Importance of SOC 2
In closing, failing SOC 2 can seriously damage trust and revenue if breaches happen. Make sure vendors secure data as diligently as you do. Confirm alignment with your high internal benchmarks.
With cyberthreats growing, don’t take chances with data security. Insist partners comply with SOC 2 to ensure threats don’t directly impact your group via third parties. SOC 2 confirmation shows commitment to key AICPA Trust Services Criteria critical for managing risk.
To further discuss SOC 2 or schedule an audit, contact our data security specialists.
With decades of combined experience guiding organizations through certification processes, we’re ready to help assess gaps and build strategies ensuring your policies fully address essential data protection needs.
Empowering You: Take action for your SOC 2 compliance
Request Your SOC 2 Consultation Today
After navigating this comprehensive guide, we hope you feel equipped to tackle SOC 2 compliance with confidence.
Our expert team is ready to guide you through the process, address your unique pain points, and ensure your organization’s security posture is robust.
Take the first step by visiting our request for proposal page.
FAQs
- What is SOC 2 compliance?
- SOC 2 compliance is a framework governed by AICPA to ensure security, availability, processing integrity, confidentiality, and privacy of customer data according to Trust Services Criteria.
- What are the 5 main categories of Trust Services Criteria?
- The 5 main TSC categories are security, availability, processing integrity, confidentiality, and privacy.
- What is the difference between a SOC 2 Type 1 and Type 2 report?
- A Type 1 report checks if controls meet standards at a point in time while a Type 2 reviews controls over 6-12 months.
- What does the security criteria cover under SOC 2?
- The security criteria cover access controls, physical controls, operational controls, risk management, and an overall security program.
- How does SOC 2 ensure system availability?
- SOC 2 ensures availability through redundant infrastructure, backup testing, capacity monitoring, and structured maintenance windows.
- What controls ensure processing integrity under SOC 2?
- Processing integrity is ensured through data validation checks, transaction logging, data integrity testing, and capacity planning.
- How is confidentiality maintained under SOC 2 standards?
- Confidentiality is maintained through least-privilege access, encryption, data classification, personnel screening, and data loss prevention.
- What are some privacy controls under the SOC 2 framework?
- Privacy controls include having a privacy policy, obtaining user consent, minimizing data collection, and enabling users to update their information.
- Who is the authority on SOC 2 compliance requirements?
- The undisputed authority on SOC 2 requirements is AICPA since they define the industry standards.
- Why is SOC 2 compliance important for organizations?
- SOC 2 is important since failing certification can seriously damage trust and revenue if breaches occur due to poor controls.