A recent survey by the Enterprise Strategy Group (ESG) revealed that 60% of organizations conduct penetration testing at least once per year, with a proactive 22% performing these tests quarterly to continuously address vulnerabilities. As businesses expand and integrate more third-party technologies, the dangers posed by cyberattacks increase significantly. Identifying and managing vulnerabilities proactively has never been more challenging.
In such scenarios, penetration testing companies can provide crucial support. They employ a systematic approach to pinpoint weaknesses, helping your business maintain a robust security posture.
What is Penetration Testing?
Penetration testing involves a simulated cyberattack on your organization’s systems to identify and exploit vulnerabilities. This pivotal process casts a wide net over web applications, networks, and even human elements via social engineering simulations.
Distinguishing Penetration Testing Vs Vulnerability Assessment
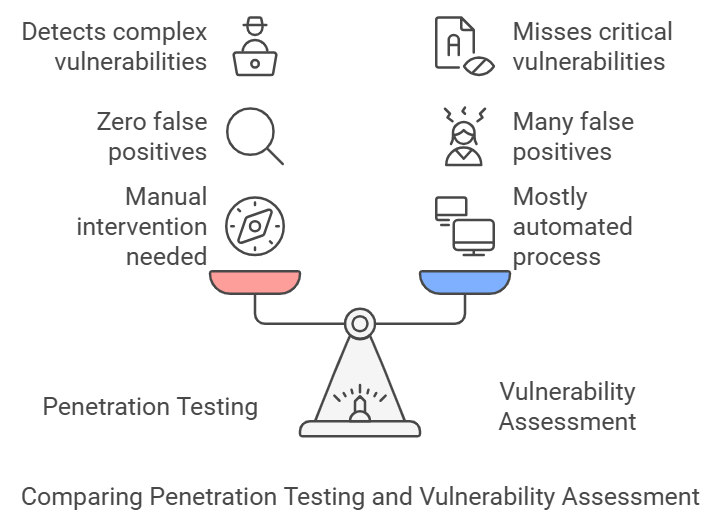
Penetration testing and vulnerability assessments present different focal points. While penetration testing deliberately exploits vulnerabilities to extract detailed insights, vulnerability assessments primarily detect and categorize vulnerabilities through mostly automated means. Manual intervention in penetration testing helps minimize false positives and uncovers business logic flaws often missed in automated scans. Both approaches are integral, often combined as VAPT (Vulnerability Assessment and Pen Testing) or in a Security Audit.
Pen Testing Types
Cloud Pen Testing With cloud technology adoption accelerating cloud environments require rigorous testing. Cloud penetration testing dissects Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) for exploitable vulnerabilities like insecure APIs and weak credentials.
Network Pen Testing Network pentesting scrutinizes network infrastructures, whether on-premises or within cloud services like Azure and AWS. It covers internal, external, and wireless network assessments to detect lapses in configurations and encryption protocols.
Web Application Pen Testing As web applications proliferate, so do potential vulnerabilities. This testing simulates attacks under varying conditions—black-box, white-box, and gray-box—to identify issues such as DDoS, SQL injections, and cross-site scripting.
API Pen Testing Given their role in communication between applications, APIs require thorough testing to protect against broken authentication, data exposure, and other critical vulnerabilities.
Mobile Pen Testing Addressing vulnerabilities in mobile applications for Android, iOS, and hybrid systems is vital. Key issues include insecure communications and weak authentication protocols.
Social Engineering Pen Testing Unlike technological testing, social engineering focuses on human vulnerabilities, employing tactics like phishing and pretexting to evaluate organizational resilience and guide training improvements.
Who Performs Penetration Testing?
Penetration testing is carried out by cybersecurity experts skilled in identifying and exploiting security flaws. These experts may be in-house staff or external specialists from VAPT companies, depending on the organization’s preference for expertise and objectivity.
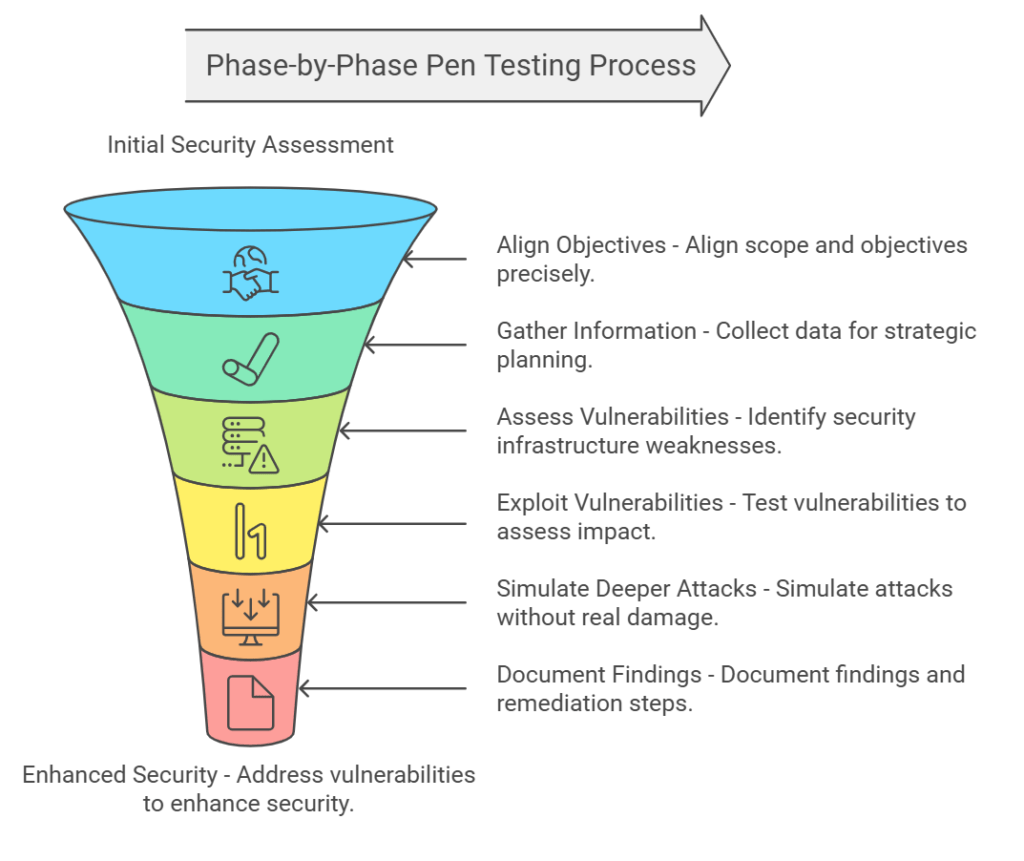
Detailed Phase-by-Phase Pen Testing Process
Pre-Engagement Analysis Align your security provider on scope and objectives before executing tests.
Information Gathering Collect publicly available data to assist in crafting effective penetration strategies.
Vulnerability Assessment Identify potential security lapses within the organization’s infrastructure.
Exploitation Exploit identified vulnerabilities to assess their impact and potential exploitation ease.
Post-exploitation Simulate deeper attacks to measure impact without causing real damage.
Reporting Document findings alongside remedial steps for management and technical teams.
Resolution Act on reported vulnerabilities to safeguard systems against breaches.
Rescanning Validate the resolution of vulnerabilities through rescanning efforts to affirm security improvements.
Strategic Approaches to Pen Testing
White Box Testing Full disclosure to testers ensures the identification of deep and complex vulnerabilities across systems.
Gray Box Testing Partial knowledge allows testers to focus keenly on specific attack vectors while avoiding unnecessary trial-and-error methods.
Black Box Testing Mimicking real-world threat actors, black box testing is often left to third parties to effectively emulate external attacks.
Also Read : Compliance Made Easy: Mastering ISO 27001 (Certification, Cost & Benefits)
Also Read : Audit-Ready Infra: SOC 2 Compliance for Robust Data Security
Benefits of Penetration Testing
Vulnerability Identification Proactively identifying exploitable vulnerabilities to prioritize security rectifications.
Enhanced Security Posture Increases the effectiveness of organizational security measures and protocols.
Compliance Achievement Aligns with industry regulations such as PCI DSS, ensuring rigorous security standard adherence.
Cost Efficiency Prevents costly breaches by addressing issues before exploitation.
Trust Building Certifications and compliance derived from regular penetration testing enhance trust among customers and partners.
Data Protection Through regular testing, organizations can safeguard sensitive data, protecting both employee and customer information from breaches.
Reputation Improvement A dedication to robust security practices, including regular penetration testing, can boost an organization’s reputation and help attract new customers and partners.
Financial Loss Prevention Considering the high cost of data breaches, estimated at $4.45 million in 2023, pen testing serves as a crucial preventative measure against financial and reputational damage.
Why Choose JCSS for Your Penetration Testing Needs?
JCSS offers comprehensive pen testing services tailored to your business, ensuring no stone is left unturned. Our team of expert security engineers deploys cutting-edge techniques to uncover even the most subtle vulnerabilities. Learn more about how JCSS can elevate your security posture and protect your digital assets today.
Who Needs Penetration Testing?
Every organization with a digital presence benefit from penetration testing, including startups, SMEs, SaaS companies, e-commerce sites, healthcare organizations, financial institutions, government bodies, and educational institutions. Regularly scheduled testing can identify and mitigate vulnerabilities before they can be exploited maliciously.
Frequency of Penetration Tests
It’s recommended to conduct pen tests at least annually, bi-annually, or subsequent to significant updates or changes to your systems. This proactive approach helps maintain security efficacy over time.
Why JCSS?
Expertise and Experience Our skilled team offer hacker-style pen testing, applying real-world tactics to explore possible entry points.
Continuous Testing Solution JCSS integrates continuous vulnerability scanning into your development workflows to catch vulnerabilities as they appear.
Regulatory Compliance Gain certification and compliance approvals from standards like SOC2, HIPAA, and ISO27001 through our detailed testing and reports.
Building Trust and Credibility Secure systems translate into increased trust with stakeholders and enhanced revenue potential.
See how JCSS’s advanced penetration testing services can safeguard your business, ensuring both security and compliance. Contact us today for a comprehensive security evaluation and take your cybersecurity strategy to the next level.
Ready to fortify your digital defenses? Contact JCSS Indonesia today for a personalized cybersecurity assessment! Let’s work together to create a secure, resilient, and prosperous future for your enterprise.
By partnering with JCSS Indonesia, you’re not just protecting your data – you’re safeguarding your business’s future. Reach out now, and let’s start building your unbreachable digital fortress!
Protect Your Network Now!
JCSS is offering a FREE limited-time security audit.
Our expert pentesters will identify vulnerabilities before hackers do.
Don’t wait – slots are filling fast!
FAQs
1. What is penetration testing, and why is it important for our organization?
Penetration testing, often referred to as “pen testing,” is a simulated cyber-attack against your organization’s systems, networks, or applications. The primary goal is to identify vulnerabilities that could be exploited by malicious actors. This proactive approach is crucial for several reasons:
- Risk Mitigation: It helps organizations understand their security posture and identify weaknesses before they can be exploited.
- Regulatory Compliance: Many industries require regular penetration testing to comply with regulations such as PCI DSS and GDPR.
- Incident Response Preparation: By simulating real-world attacks, organizations can better prepare for potential breaches and improve their incident response strategies.
2. How is penetration testing different from vulnerability scanning?
While both penetration testing and vulnerability scanning aim to enhance security, they differ significantly:
| Aspect | Vulnerability Scanning | Penetration Testing |
|---|---|---|
| Approach | Automated scans for known vulnerabilities | Manual or automated simulated attacks to exploit flaws |
| Depth | Surface-level identification of vulnerabilities | In-depth analysis of security measures |
| Outcome | Reports potential weaknesses | Detailed insights into exploitable vulnerabilities |
Vulnerability scanning acts as an early warning system, while penetration testing provides a more realistic assessment of security effectiveness
3. What types of pentesting services are available?
Organizations can choose from various types of penetration testing services, including:
- Network Penetration Testing: Focuses on identifying vulnerabilities in network infrastructure.
- Web Application Penetration Testing: Targets web applications to find security flaws.
- Mobile Application Penetration Testing: Assesses mobile apps for vulnerabilities.
- Physical Security Testing: Evaluates physical access controls and security measures.
- Social Engineering Testing: Tests employee awareness and susceptibility to manipulation.
- IoT Penetration Testing: Focuses on Internet of Things devices and their security
4. How do we choose the right pentest provider? What qualifications and certifications should we look for?
Selecting a suitable penetration testing provider involves several key considerations:
- Certifications: Look for providers with recognized certifications such as OSCP (Offensive Security Certified Professional), CEH (Certified Ethical Hacker), or GIAC GPEN (GIAC Penetration Tester).
- Experience: Evaluate their track record in your industry and the specific types of testing required.
- Methodologies: Ensure they follow industry-standard methodologies for penetration testing.
- Reputation: Check client testimonials and case studies to assess their effectiveness
5. How long does a penetration test typically take, and how will it impact our business operations?
The duration of a penetration test can vary based on scope but generally takes anywhere from a few days to several weeks. The impact on business operations is typically minimal as tests are planned during off-hours or in phases. However, some systems may experience temporary slowdowns during active tests. Clear communication with the provider about scheduling can help mitigate disruptions
6. How often should our organization conduct pentesting?
Organizations should conduct penetration testing at least annually or more frequently if:
- Significant changes are made to the IT environment (e.g., new applications or infrastructure).
- New threats emerge that could affect the organization.
- Compliance requirements mandate more frequent assessments.
7. What will happen if vulnerabilities are found during the penetration test?
If vulnerabilities are discovered, the provider will typically deliver a detailed report outlining:
- The nature of each vulnerability.
- Potential impacts if exploited.
- Recommended remediation steps.
Organizations should prioritize addressing these vulnerabilities based on risk assessment and potential impact on operations.