What is API Security
Application Programming Interfaces (APIs) are protected from unauthorized access, abuse, and possible risks by procedures and security measures. APIs are interfaces that allow different software applications to communicate with each other, exchange data, and perform various functions.
API security has become a vital part of overall application security as they have grown in importance in modern software development.
Why API Security is Important
APIs (Application Programming Interfaces) have become an essential part of modern software development. They allow different applications to communicate with each other, enabling developers to create complex systems that are more efficient and scalable.
However, with the increasing use of APIs, the need for API security has become more critical than ever. In this article, we will discuss the API security checklist and best practices that can help you secure your APIs.
Some of our suggestions are based on industry-leading security criteria, such as the OWASP API Security Top 10 list.
The rest stems from our experience working with organizations of all sizes.
API Security Best Practices & API Security Standards
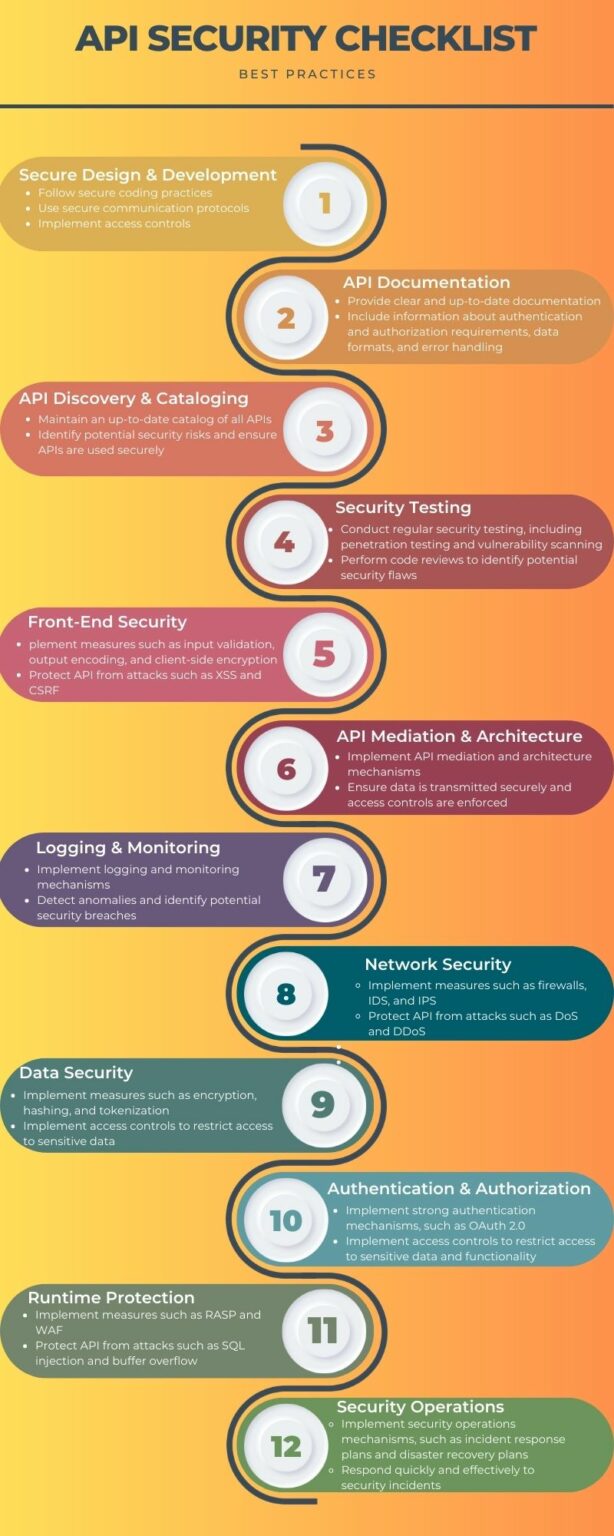
Secure Design & Development
The first step in securing your API is to ensure that it is designed and developed with security in mind. This means that you should follow secure coding practices, such as input validation, output encoding, and error handling.
The OWASP Application Security Verification Standard (ASVS) is a good source that is useful for all types of application designs. You should also use secure communication protocols, such as HTTPS, to encrypt data in transit. Additionally, you should implement access controls to restrict access to sensitive data and functionality.
API Documentation
API documentation is essential for developers who want to use their API. It should be clear, concise, and up to date. It should also include information about identification and clearance requirements, data formats, and error handling. By providing comprehensive documentation, you can help developers use your API securely and avoid common security pitfalls.
API Discovery & Cataloging
API discovery and cataloging are critical for managing your APIs. You should maintain an up-to-date catalog of all your APIs, including their endpoints, data formats, and identification requirements. This will help you identify potential security risks and ensure that your APIs are used securely.
Security Testing
Security testing is essential for identifying flaws in your API. You should conduct regular security testing, including penetration testing and compromise scanning, to identify potential security risks. You should also perform code reviews to identify potential security flaws in your API code.
Front-End Security
For your API to be protected against client-side threats, front-end security is crucial.
You may use the following security measures to guard your website against damaging attacks like cross-site scripting and cross-site request forgery:
-double-checking the information, you receive
-ensuring the information, you send is secure
-keeping your personal information secure on your own device.
Logging & Monitoring
Logging and monitoring are essential for detecting and responding to security incidents. You should implement logging and monitoring mechanisms to track API usage, detect anomalies, and identify potential security breaches. You should also implement alerting mechanisms to notify you of potential security incidents.
API Mediation & Architecture
API mediation and architecture are essential for managing the flow of data between different applications. You should implement API mediation and architecture mechanisms to ensure that data is transmitted securely and that access controls are enforced. You should also implement rate limiting mechanisms to prevent API abuse.
To begin, consider the four rate-limiting options listed below to properly control your resources without interfering with user experience:
- Leaky Bucket: an algorithm that approaches rate limiting with queues -first in, first out
- Token Bucket: an algorithm that approaches rate limiting with fixed capacity buckets
- Fixed Window: time-based rate limiting algorithm that processes requests based on time limits
Sliding Log: time-stamped logs for each request
Network Security
Network security is essential for protecting your API from attacks that originate from the network.
Fortify your API against threats with an arsenal of defenses like DDoS, DoS, firewalls, IDS, and IPS.
Data Security
Data security is essential for protecting sensitive data that is transmitted through your API. You should implement measures such as encryption, hashing, and encoding to protect sensitive data. You should also implement access controls to restrict access to sensitive data.
When hackers master your API’s intricacies and hole-spotting, their malicious success soars. Once they uncover your servers’ Apache affiliation, breaching your defenses through familiar security flaws becomes child’s play. Prevent such mishaps by scrutinizing API sections prone to excessive data exposure weakness.
- Error pages
- URL strings
- API responses
- Data in transit
- Data at rest
- The client – especially when it comes to filtering data
Ensure user safety with APIs by preventing client-side data filtering, optimizing response sizes, and embracing OpenAPI and RAML standards to minimize excessive data exposure.
Authentication & Authorization
Authentication and authorization are essential for ensuring that only authorized users can access your API. You should implement strong identification mechanisms, such as OAuth 2.0, to authenticate users. You should also implement access controls to restrict access to sensitive data and functionality.
Runtime Protection
Runtime protection is essential for protecting your API from attacks that occur during runtime.
Fortify your API against malicious threats like buffer overflow and SQL injection by implementing safeguards such as web application firewalls (WAF) and runtime application self-protection (RASP).
Security Operations
Security operations are essential for managing security incidents and responding to security breaches.
Fortify your defenses with swift and savvy security operations, armed with incident response plans and disaster recovery strategies, for a vigilant and efficient shield against security breaches.
External Resources
External resources, such as third-party libraries and APIs, can introduce security risks into your API. You should carefully evaluate external resources before using them in your API. You should also implement measures such as input validation and output encoding to protect your API from attacks that originate from external resources.
API Security Checklist
For more API Checklist you can read API Security Checklist: What You Need To Know from Apisec who have explained a lot more in detail about how “Any user input can be potentially used to bypass your API security systems since it’s often used to call other code”.
Conclusion
In conclusion, the API Security checklist above covers many different API exposure in detail, but it doesn’t provide enough protection against the constantly evolving strategies of hackers.
This mostly has to do with the fact that every API is a complicated system where practically every component may be misused by hackers in some way.
Additionally, despite how thorough your checklist is, business logic defects, the most hazardous kind of API weakness, are not adequately addressed.
Sign up for the API Security Services form on our site and our experts will help you plan and audit your organization.

